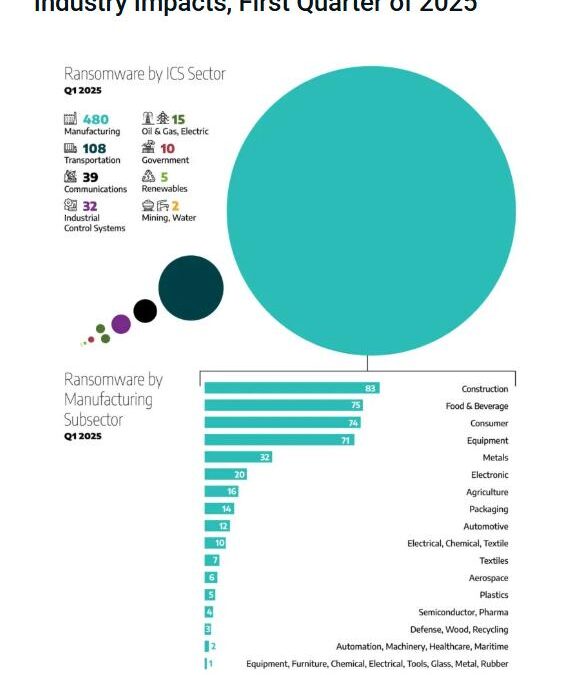
A report highlights that the industrial sector has been the most affected by ransomware crimes. Specifically, in these last months of 2025, up to 480 industries of this type or factories have been attacked.
By subsectors, we observe that in the metals sector, these damages have affected 32 companies.
These news, of course, will not appear in the novelties section. It’s not good press to show companies’ vulnerabilities, but reports like this one by Dragos can be a good warning to take precautions to prevent cyber attacks from causing irreparable damage to our orders, sales, or technology.
Main findings of the report:
- Ransomware attacks increased from about 600 in the fourth quarter of 2024 to 708 in the first quarter of 2025.
- The manufacturing sector was the hardest hit, accounting for 68% of cases. Within this sector, the construction, food and beverage, consumer goods, and industrial equipment subsectors concentrated the most activity.
- Oceania recorded 14 incidents, most in Australia (13), and one in New Zealand. North America and Europe also saw significant increases.
- Although no new variants specifically targeting industrial control systems (ICS) emerged, large-scale operational disruptions were reported.
- Emerging techniques include the use of AI-based malware, encryption-less extortion tactics, involvement of state actors, and advanced evasion of EDR solutions.
- Methods such as AI-driven phishing, exploitation of zero-day vulnerabilities, abuse of remote access, and credential theft also persist.
- The Cl0p group significantly increased its activity, exploiting flaws in the Cleo Managed File Transfer platform.
- The convergence between IT and OT environments continues to intensify the consequences of attacks.
- Disinformation and unverified statements by criminal groups hinder defensive strategies.
In detail, manufacturing reported 480 attacks in the first quarter, compared to 424 in the previous period. The food and beverage subsector was the most affected, with 75 incidents (16%). Attackers exploited weaknesses in remote access, credential management, and supply chain security, which exacerbated operational damage and hindered responses.
Recommendations and defensive measures
Dragos emphasizes the importance of having proactive defensive measures and early detection capabilities. Applying rules based on robust threat intelligence allows security teams to identify signs of attacks in early stages, reducing the risk of serious disruptions.
The report recommends organizations adopt key measures such as:
- Implementation of robust multi-factor authentication (MFA).
- Intensive monitoring of critical network areas.
- Secure offline backups.
- Reinforced protocols for remote access management.
Additionally, it is essential to offer continuous training to personnel, regularly review network architecture, and use AI-based detection solutions. These actions help mitigate complex threats such as AI-generated phishing, encryption-less extortion, or nation-state-linked attacks, like those attributed to the Qilin group. It is also recommended to validate threat information to counter deceptive practices, such as those associated with Babuk 2.
In a context where the ransomware ecosystem becomes more fragmented and sophisticated, anticipatory defensive strategies, agile information sharing, and collaboration between key actors are fundamental to protect industrial operations and critical infrastructures. Strengthening cybersecurity in IT/OT convergence, protecting vulnerable supply chains, and improving notification systems will contribute to increasing resilience against these persistent threats.